IP (Internet Protocol) is a network layer protocol responsible for addressing and routing data packets between devices across different networks. It provides a best-effort, connectionless delivery system, meaning it does not guarantee packet arrival, order, or integrity. IP is the backbone of the internet and works with protocols like TCP and UDP for data transmission.
Key Functions:
- Assigns IP addresses to devices.
- Routes packets across multiple networks.
- Handles fragmentation and reassembly of large packets.
- Works with IPv4 (32-bit addresses) and IPv6 (128-bit addresses).
Philosophy Behind IP Development
1. Simplicity and Scalability
- IP was designed to be simple, making it scalable across diverse networks.
- It does not provide built-in reliability mechanisms, leaving those to higher-layer protocols like TCP.
2. Connectionless Communication
- Unlike circuit-switched networks (e.g., telephone networks), IP is connectionless and stateless, meaning each packet is treated independently.
3. End-to-End Principle
- The intelligence of the network is pushed to the edges (i.e., the hosts), while the core routers focus only on forwarding packets.
4. Flexibility and Interoperability
- IP allows different types of networks (wired, wireless, satellite, etc.) to communicate.
- It was designed to be independent of the underlying hardware.
5. Decentralization
- There is no central control over IP routing, making it resilient to failures.
- Each network device determines the best path for a packet dynamically.
Key Terms in Internet Protocol (IP)
- Internet Protocol (IP) – A network-layer protocol responsible for addressing and routing packets between devices.
- Datagram – A unit of data transmission that is handled independently without guarantees.
- IP Address – A unique numerical identifier for a device in a network.
- Routing – The process of directing packets across multiple networks to reach a destination.
- Fragmentation – Splitting large packets into smaller ones to accommodate different network limits.
- Time to Live (TTL) – A counter that decrements at each router hop to prevent indefinite looping.
- Checksum – A verification method to detect errors in the IP header.
- Best-Effort Delivery – No guarantees of packet arrival, order, or integrity.
- IPv4 vs IPv6 – IPv4 (defined in RFC 791) is limited to 32-bit addresses, while IPv6 (a later development) expands to 128-bit addresses for scalability.
Breakdown of IPv4 Header Fields
IPv4 is a connectionless protocol that helps in routing packets across networks. The IPv4 header consists of mandatory fields, as shown in the image.
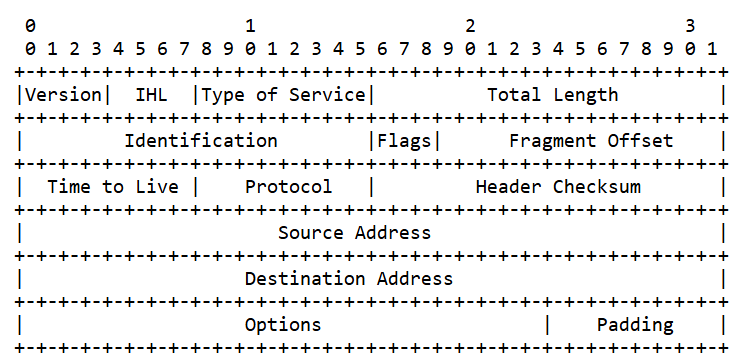
1. Version (4 bits)
- Indicates the IP version being used. Since this is IPv4, the value is always
4. - Analogy: Just like a letter marked as “Priority Mail” or “Regular Mail,” this tells the system what kind of protocol is in use.
2. IHL (Internet Header Length) (4 bits)
- Specifies the length of the IP header in 32-bit words.
- Minimum value:
5(which means 20 bytes), Maximum value:15(which means 60 bytes). - Analogy: Think of this as specifying whether the package label has just a basic address or additional instructions.
3. Type of Service (TOS) (8 bits)
- Defines how the packet should be prioritized (e.g., for speed, reliability, or low delay).
- Modern networks often use this field for Quality of Service (QoS).
- Example: Streaming a video needs low delay, while sending an email can tolerate some delay.
4. Total Length (16 bits)
- Specifies the entire packet size (header + data) in bytes.
- Minimum size:
20 bytes, Maximum size:65,535 bytes. - Analogy: Like writing the total weight of a package to ensure it can be handled properly.
5. Identification (16 bits)
- A unique ID assigned to each packet, useful when large data is broken into smaller pieces (called fragments).
- Example: When sending a 10MB file over the internet, it is divided into smaller parts, each carrying the same ID.
6. Flags (3 bits)
- Controls whether the packet can be fragmented.
- DF (Don’t Fragment): If set, the packet must not be broken down.
- MF (More Fragments): If set, this is not the last fragment.
- Analogy: Similar to a shipping label with instructions like “Do Not Bend” or “Handle with Care.”
7. Fragment Offset (13 bits)
- Indicates the position of a fragmented packet’s data in the original message.
- Example: If a large email attachment is broken into smaller parts, this field helps the receiver put them back in order.
8. Time to Live (TTL) (8 bits)
- Limits how long a packet can travel before being discarded.
- Each router it passes through decreases this value by 1. If it reaches
0, the packet is dropped. - Analogy: Like an expiration date on perishable food—after a certain time, it is no longer usable.
9. Protocol (8 bits)
- Indicates the next protocol used in the data payload.
- Examples:
1→ ICMP (ping requests)6→ TCP (web browsing, emails)17→ UDP (video streaming, online gaming)
- Analogy: Like specifying if the package contains a book, clothes, or electronics.
10. Header Checksum (16 bits)
- A value used to check if the header was corrupted during transmission.
- Example: Similar to scanning a barcode to verify a product’s authenticity.
11. Source Address (32 bits)
- The IP address of the sender.
- Example: If a message is sent from
192.168.1.1, this field stores that address.
12. Destination Address (32 bits)
- The IP address of the receiver.
- Example: If a packet is going to
8.8.8.8(Google’s DNS server), this field contains that address.
13. Options (Variable length)
- Used for additional controls like security, debugging, or timestamps.
- Not commonly used in most modern networks.
14. Padding (Variable length)
- Extra bits added to make the header size a multiple of 32 bits.
- Analogy: Like adding extra packing peanuts to fill up a box.
Illustrative Example: Sending an Email
Imagine you send an email from [email protected] to [email protected].
- Version & IHL: Specifies that IPv4 is being used and how long the header is.
- Type of Service: Prioritizes email over other traffic.
- Total Length: The entire email’s data size is calculated.
- Identification, Flags & Fragment Offset: If the email is large, it gets split into smaller packets.
- TTL: Ensures the email does not get stuck in an endless loop on the internet.
- Protocol: Uses TCP (since email needs reliable delivery).
- Checksum: Ensures the email’s data was not corrupted.
- Source & Destination Address: The sender (
192.168.1.1) and recipient (203.0.113.5) are specified.
Each router on the internet reads this header to properly forward the packet until it reaches its final destination!
Conclusion
The IPv4 header is like a package label that ensures information reaches its destination accurately. While it may seem complex, breaking it down into simple components makes it easier to understand. Next time you send an email, watch a video, or browse the web, remember that IPv4 headers are working behind the scenes to make it all possible!
References:
